- A hardware wallet is a tangible apparatus meticulously engineered to securely retain private keys in an offline environment, thereby fortifying them against potential perils originating from the online realm.
- Hardware wallets offer numerous advantages in terms of ensuring the utmost security and safeguarding the storage of cryptocurrencies.
- Although hardware wallets are widely regarded as a highly secure method for storing cryptocurrencies, it is important to acknowledge that they are not entirely devoid of potential risks. It is advisable to acquaint oneself with essential safety guidelines pertaining to the secure utilization of a hardware wallet.
What Is a Hardware Wallet?
A hardware wallet is a tangible apparatus meticulously engineered for the exclusive purpose of securely safeguarding the private keys associated with cryptocurrencies in an offline environment. Private keys serve as the cryptographic tool utilized to authenticate and authorize transactions. Consequently, possessing control over one’s private keys equates to possessing control over one’s cryptocurrency holdings.
Hardware wallets, commonly known as cold wallets, serve the purpose of safeguarding private keys against potential digital vulnerabilities, including but not limited to malware or unauthorized access by hackers. This is achieved by employing a mechanism that ensures the keys remain exclusively within the confines of the device during the internal transaction signing process. This particular approach renders them as one of the more robust means for safeguarding cryptocurrency.
On the contrary, software wallets, commonly referred to as hot wallets, encompass online applications that are installed on various devices such as computers or smartphones. These wallets provide enhanced accessibility, albeit at the cost of increased susceptibility to internet-based attacks.
How Does a Hardware Wallet Work?
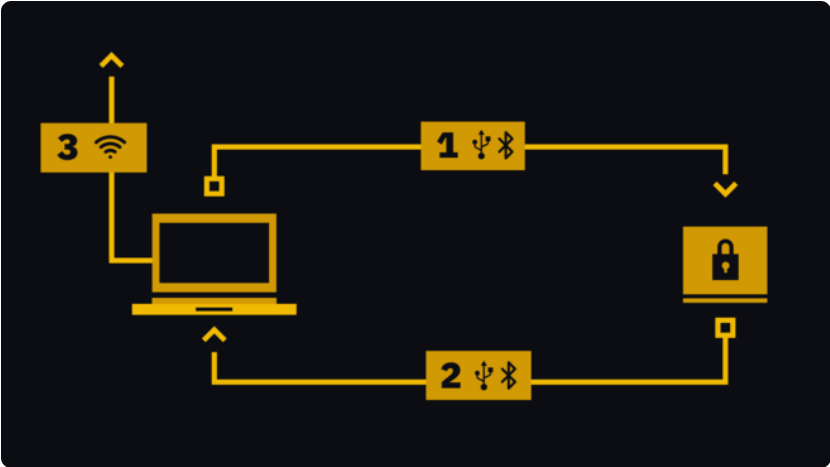
Given that hardware wallets maintain an offline state consistently, it is imperative to employ them in conjunction with an additional device that remains connected to the Internet. Hardware wallets are designed with the capability to establish a secure connection with PCs or smartphones, ensuring the non-disclosure of the private key, even in instances where the connected devices may have been compromised by malicious software. Subsequently, the user engages with software that facilitates the viewing of their account balance and execution of financial transactions.
Upon the initiation of a transaction by the user, said transaction is subsequently transmitted to the designated hardware wallet, denoted as “1” in the accompanying diagram. It is important to acknowledge that the transaction remains incomplete as it necessitates the signature from the private key stored within the device. The confirmation of the accuracy of the amount and address is duly acknowledged by users upon receiving a prompt on the hardware device. Subsequently, the transaction is duly endorsed and transmitted back to the software (2), which subsequently disseminates it across the network of the respective cryptocurrency (3).
Ten Safety Precautions to Take When Using Hardware Wallets
When utilizing hardware wallets, it is important to consider the advantages and potential drawbacks. Here are 10 essential tips to enhance security while using hardware wallets.
- Purchase a hardware wallet from a reputable vendor. To ensure the integrity of your hardware wallet, it is advisable to acquire it exclusively from the manufacturer or a reputable retailer.
- Make sure the latest version of the program is installed. It is important to regularly update the firmware of your wallet. Updates are frequently issued by manufacturers to enhance security and functionality.
- Do not disclose your recovery phrase under any circumstances. The recovery phrase holds equivalent power to the private key. In the event that another individual gains access, they may assume control over your cryptocurrencies. It is important to exercise caution and refrain from sharing personal information when approached by others who may request it.
- Ensure the utmost security and offline storage of your recovery phrase. It is important to ensure the safekeeping of your recovery phrase by storing it in a secure and offline location. Avoid storing it digitally or online to minimize the risk of potential hacking.
- Ensure the utilization of a robust PIN. Ensure the security of your device by implementing a robust PIN to prevent unauthorized access. Avoid using easily guessable PINs such as “1234” or “0000”.
- Ensure that addresses are verified for accuracy. It is crucial to consistently verify the recipient’s address when conducting cryptocurrency transactions. Clipboard address alteration is a potential consequence of malware.
- Verify transactions on the device. It is important to ensure that you verify the transaction details on your hardware wallet’s screen prior to confirming, rather than solely relying on your computer or smartphone screen.
- Ensure the security of your wallet. It is crucial to handle your hardware wallet with the same level of care and caution as you would when dealing with valuable jewelry or significant sums of cash. Ensure that the item is stored in a safe and protected area when it is not being utilized.
- It is advisable to contemplate the utilization of a passphrase. To enhance security, certain wallets offer the option to include a passphrase alongside the PIN. A concealed wallet is effectively formed. In the event that the passphrase is forgotten, it is important to note that recovery is not possible. Therefore, it is advised to exercise caution when utilizing this feature.
- Utilize reliable computer systems. It is advisable to exclusively link your hardware wallet to trusted computers with robust security measures. It is advisable to refrain from connecting your hardware wallet to devices solely for the sake of convenience.
Conclusion
Hardware wallets offer a great balance of security and user-friendliness for cryptocurrency management. A highly secure environment is provided for offline storage of digital assets, ensuring safe transactions even on compromised computers. Like any security solution, they aren’t completely foolproof and need careful handling and responsible usage by the user.
Private keys or recovery phrases should never be shared. It is recommended to store them securely and offline. Purchasing from trusted sources, using strong PINs, updating wallet firmware regularly, and verifying transaction details are important for asset security.
Hardware wallets, while important for cryptocurrency security, require users to be aware of potential risks and losses. Understanding technology and following best practices can help reduce these risks.


